
Our personal email accounts enable us to send and receive messages instantly with people all around the world. While we primarily use our email accounts for communications purposes, many of us use it to sign up for accounts such as online banking, online shopping, social networks, and even alternative email accounts. But have you considered the possibility that your personal email account could be the weakest link? By “weakest link”, we mean that a compromised email account could potentially result in the accounts connected to it being compromised too. That’s why it’s important to address email security from the get go.
Where the weakness lies
The way you sign into your personal email account is by entering in your username and password then clicking “Sign In”. For some email providers, in the event you somehow can’t access your account because you do not remember your password, you can simply click on “Forgot password” or “I can’t access my account”. From there you’re presented with a security question that you must answer correctly, where upon doing so you’re prompted to create a new password before gaining access into your account. Unfortunately, this is where the weakness lies.
Your email account may be secured by the most complicated and complex password, but that alone is not enough to keep hackers out. Hackers can simply try their luck by clicking on the same “Forgot password” link or “I can’t access my account” as you would if you forgot your password and see if they can guess the answer to your security question. After all, “fluffy” is much easier to guess than “!Am7h3R3a7N8p5ter”.
So, how exactly could a hacker compromising your personal email account lead to your online accounts associated with it being potentially compromised as well?
How your other online accounts could be compromised
Let’s first assume a hacker has gained access to your personal email account. There’s now a good amount of information he might be able to extract from your account. If you’re the type of person who emails yourself the login credentials for your online accounts, then you’ve practically handed the hacker the login credentials for those accounts too. Even if you’re not the type to email yourself login credentials, the online accounts connected to your personal email account could still be compromised.
Let’s use Facebook as an example. Assuming a hacker has gained access to the email account connected with your Facebook account, they could go to Facebook and simply initiate a password reset. Upon entering that email address and clicking on “Continue”, Facebook will ask “How would you like to reset your password?” along with the option to “Email me a link to reset my password”. Though some of the characters in the email address given are masked by the asterisks symbol, it’s quite easy to determine if the email address shown is the same one the hacker has just gained access to.
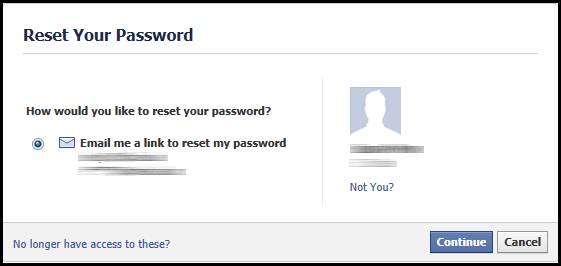
After clicking on “Continue”, Facebook sends a code to the email addressed associated with the Facebook account.
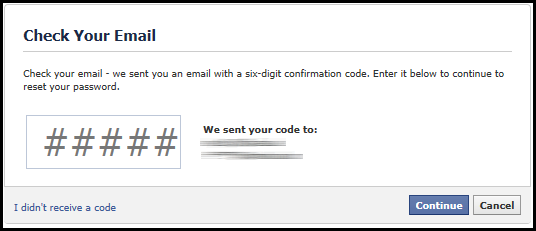
Since the hacker already has gained access to your personal email account, they can easily click on “Continue” and simply wait for the password reset email in your inbox.
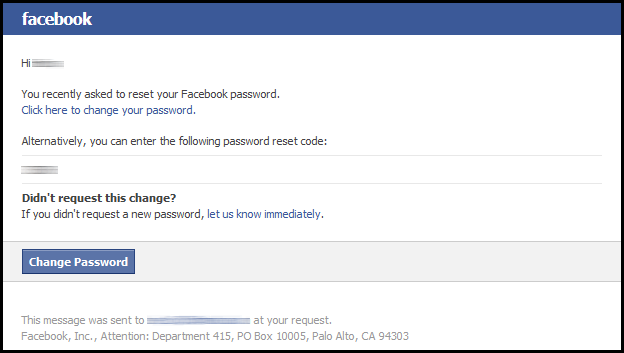
After receiving the code from the password reset email from Facebook and entering it into the field, the hacker is prompted to choose a new password. At this point, not only has the hacker gained access to your account, but you’ve also lost access since the password you once used to log in is now only known to the hacker.
How to strengthen the security of your email accounts
Don’t share too much online
Let’s first revisit “fluffy” mentioned above that was used as the answer to your email’s security question. How did the hacker manage to guess “fluffy” as the answer to your security question?
Let’s take a look at a sample list below of security questions you might be presented with. You can see that “What was your first pet’s name?” is listed. In fact, you probably could answer many of these questions listed below for a friend or family member.

One thing a hacker might do is search the Internet for information to aid in guessing the answer to your security question. Social networks such as Facebook and LinkedIn are a goldmine of personal information that could be exploited by someone with malicious intent. If you have a photo of your dog Fluffy on your Facebook page, it’s not a good idea to use “fluffy” as the answer to a security question for any of your online accounts. Or if the answer to your security question is your favorite author, then it’s not a good idea to publically announce on social networks that your favorite author is Tom Clancy. You get the idea.
Enable two-factor authentication for your email accounts
If at all possible, we recommend not relying on security questions as a tool to gain access to your email account in the event you do forget the password to your account. Even if you choose to create your own security question rather than relying on default question that’s provided to you from your email service provider, the fact is the answer to your security question is still guessable. The fact is a security breach associated with your email service provider could result in your email and password being exposed.
Here is where two-factor authentication comes into play.
Two-factor authentication requires an additional factor, such as a passcode sent to your mobile phone, to be entered in before access is allowed to an account. This additional security measure is triggered when a login has been initiated by an unknown browser or device. The beauty of two-factor authentication is that it really doesn’t matter if the hacker got hold of your actual password. Without the additional factor, the code sent to your phone, the hacker simply cannot gain access to your account. Below are links not only to enabling two-factor authentication for your email accounts but also for your Facebook and LinkedIn account.
• How to turn on two-factor authentication for your email accounts
• How to turn on Login Approvals for Facebook
• How to turn on two-step verification for LinkedIn
Although many email service providers are doing away with security questions due to its inherent flaws, some still utilize this feature. With that said, we suggest you to check if they offer two-factor authentication or not. Also, be sure to check with your other online accounts, such as for online banking and credit card, investment and trading, and shopping, to see if they offer two-factor authentication. It may be less convenient for you to have to take an additional step to gain access to your account, but you’ll be glad you did knowing you have another layer of security guarding your online accounts!