Subscribe to our newsletter!
Stay updated with the latest security news, tips, and promotions.

Your iPhone or iPad probably has your entire life on it—from photos, apps, contacts, and communications. What would you do if it is ever stolen?
There are some preemptive measures you can take to make the loss less traumatic in the event your device does get stolen.
Continue Reading… What to Do When Your Device is Stolen
While social media sites such as Facebook and Twitter make it easy to share things with your friends, they also make it easy to log in to various services and applications, too. As authentication brokers, Facebook and Twitter let users use their account credentials to sign into third-party sites. To do so, the user has to give permission for those sites to access their profile data.
Facebook is a full-blown apps ecosystem. You may have added an app to take advantage of a promotion or contest, played a game, or added new functionality such as music streaming. In most cases, it just means the app developer has access to some of your profile data. In the worst-case scenario, a malicious developer behind the service can use your account to send out spam.
Continue Reading… What Apps Have Access to Your Facebook and Twitter?
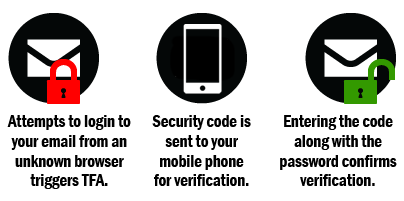
Our email accounts contain a ton of information about ourselves. We sign up for bank accounts, buy things online, and communicate with others using our email addresses. And the only thing keeping the attackers out is the strength of our passwords.
No matter how complex the passwords are, they are not foolproof. The attackers have cracking tools at their disposal and other tricks to get access to our accounts. Two-factor authentication prevents attackers from getting in even when they’ve gotten our passwords.
Continue Reading… How to Turn on Two-factor Authentication for Your Email Accounts
Account hijacking is a big problem on Facebook, where attackers manage to guess—or brute-force—your passwords. Two-factor authentication can help make it harder for criminals to take over your account.

Android devices seem to be continually under attack, with new reports of malware almost every day. However, the biggest threats against your Android phone or tablet aren’t malware, but rather unauthorized users who may access your information.
Continue reading… 7 Ways to Protect Your Android Device